PowerShell Solution: Install PFX certificate on servers
Problem
As you may have guessed, this post will be about installing certificates using PowerShell.
Every year as someone working with identity topics, I am tasked with renewing certificates across the environment. Many services relies fully on valid certificates in order to function securely.
One critical service in particular that this scenario will cover is: Active Directory Federation Services, ADFS.
In most cases, you will have multiple ADFS servers, meaning, if your not automating already, you will need to install the SSL certificate manually (no fun experience on 10+ servers).
There’s more to say regarding specifically ADFS SSL certificates, that this post will not cover, however an installation will be needed in many of those scenarios as well.
Solution
This solution covers how one could do this for ADFS servers, however it carries over to other services that requires a valid certificate as well.
To generate an pfx file out of an external certificate, I recommend using The Digicert Cert Utility to generate the CSR (Certificate Signing Request) on the root server. Then simply import it using the digicert tool, and export the certificate to a .pfx file.
Here’s an example of how to export an already installed certificate as a PFX file:
$PfxPw = (Read-Host -Prompt 'Enter a password' -AsSecureString)
Get-ChildItem -Path cert:\localMachine\my\<thumbprint> | Export-PfxCertificate -FilePath C:\Cert\ssl_cert.pfx -Password $PfxPwIt’s important that the certificate gets imported on the server where the CSR was generated, in order to have a valid public/private keypair.
What we need to start out is:
- The ADFS Root server with the pfx certificate exported
- Access to all ADFS servers
- WinRM/PowerShell remoting enabled environment
# Local path to the certificate
$PFXPath = 'C:\Cert\ssl_cert.pfx'
# Credential object, we only use the password property
$Creds = Get-Credential -UserName 'Enter PFX password below' -Message 'Enter PFX password below'
# Path of the remote server we will copy to
$ServerCertPath = "C:\Cert\"
$InternalServers = "SERVER1", "SERVER2", "SERVER3"
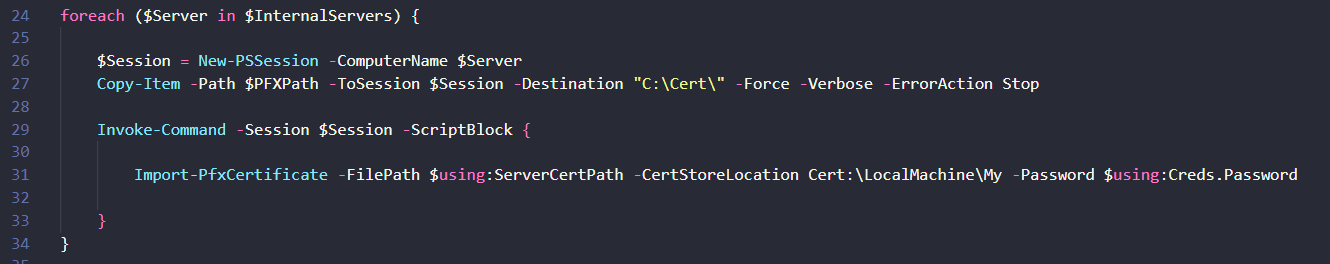
foreach ($Server in $InternalServers) {
# Creates a remote session
$Session = New-PSSession -ComputerName $Server
# Copies the certificate to the remote session
Copy-Item -Path $PFXPath -ToSession $Session -Destination $ServerCertPath -Force -Verbose -ErrorAction Stop
# Imports the pfx certificate using the credentials provided remotely
Invoke-Command -Session $Session -ScriptBlock {
Import-PfxCertificate -FilePath $using:ServerCertPath -CertStoreLocation Cert:\LocalMachine\My -Password $using:Creds.Password
}
}Small Talk
And just like that, you’ve saved truckloads of time every year using PowerShell.
I highly recommend checking out more cmdlets based from the pki and Microsoft.PowerShell.Security module. The script above displays how one can tackle a .pfx certificate, but using Import-Certificate, you could do similar things with .cer files.
Also, one could eliminate the need for generating a password with using something like Microsoft.PowerShell.SecretManagement. This module translates well into a lot of cmdlets in the pki/security module.