Solution: Restore Deleted Private key for EFS Encrypted Files
Problem
You have encrypted files using the “File > Properties > Advanced > Encrypt content to secure data” feature in Windows, and have lost your certificates in your personal certificate store.
Solution
A solution to this problem is to restore the private key used for encrypting your file system (EKU: Encrypting File System 1.3.6.1.4.1.311.10.3.4 ) that was generated upon encrypting your files.
The keypair to this certificate is stored in your Personal certificate store, luckily a copy of the public key is stored in your LocalMachine certificate store. This means we can restore the private key and enable decryption as long as the computer has not been reinstalled or lost.
Step-by-step
- This file is currently unecrypted. Let’s encrypt is using the method discussed
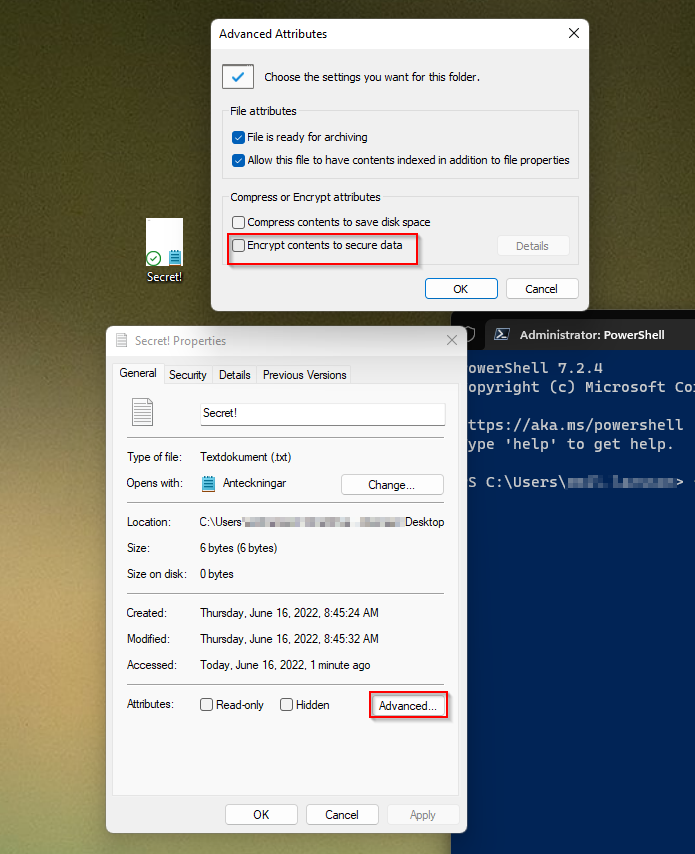
Rightclick the file > properties > advanced > encrypt content..
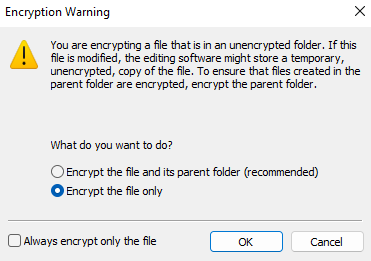
I will select ‘Ecrypt the file only’ in this case
![]()
The lock symbol indicates that the file is successfully encrypted. Under the hood, windows generated a self-signed certificate with a private/public keypair in my personal store and a certificate in my localmachine/addressbook only containing a public key.
- Verify the certificates
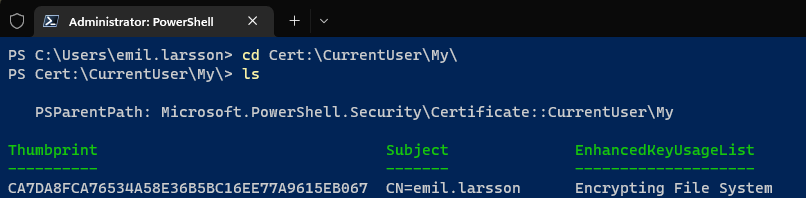
Let’s verify it’s private key:
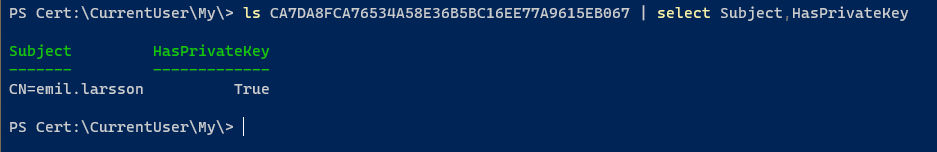
Let’s verify the localmachine/addressbook certificate:
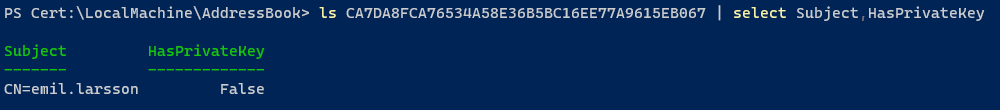
HasPrivateKey: False - tells us this certificate lacks the private key, and is somewhat useless for the decrypting of our file. We will now move on to the issue at hand
- Delete the current users private key to simulate the issue
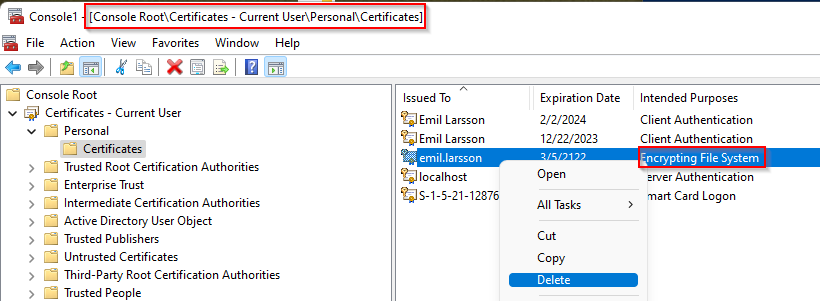
Let’s try to query the certificate store to verify the lack of this deleted certificate
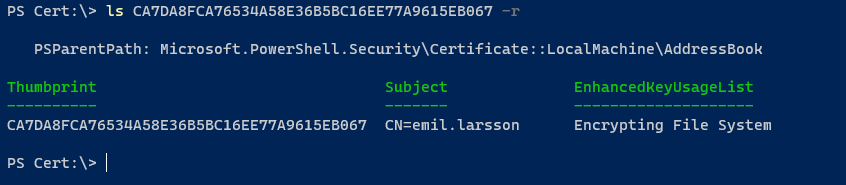
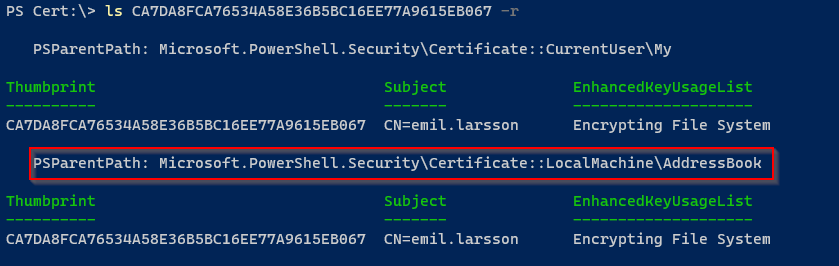
We are recursivly looking for the certificate in the root of the certificate store, and we only got one hit. Meaning the private/public keypair has been removed, together with the ability to decrypt our file:

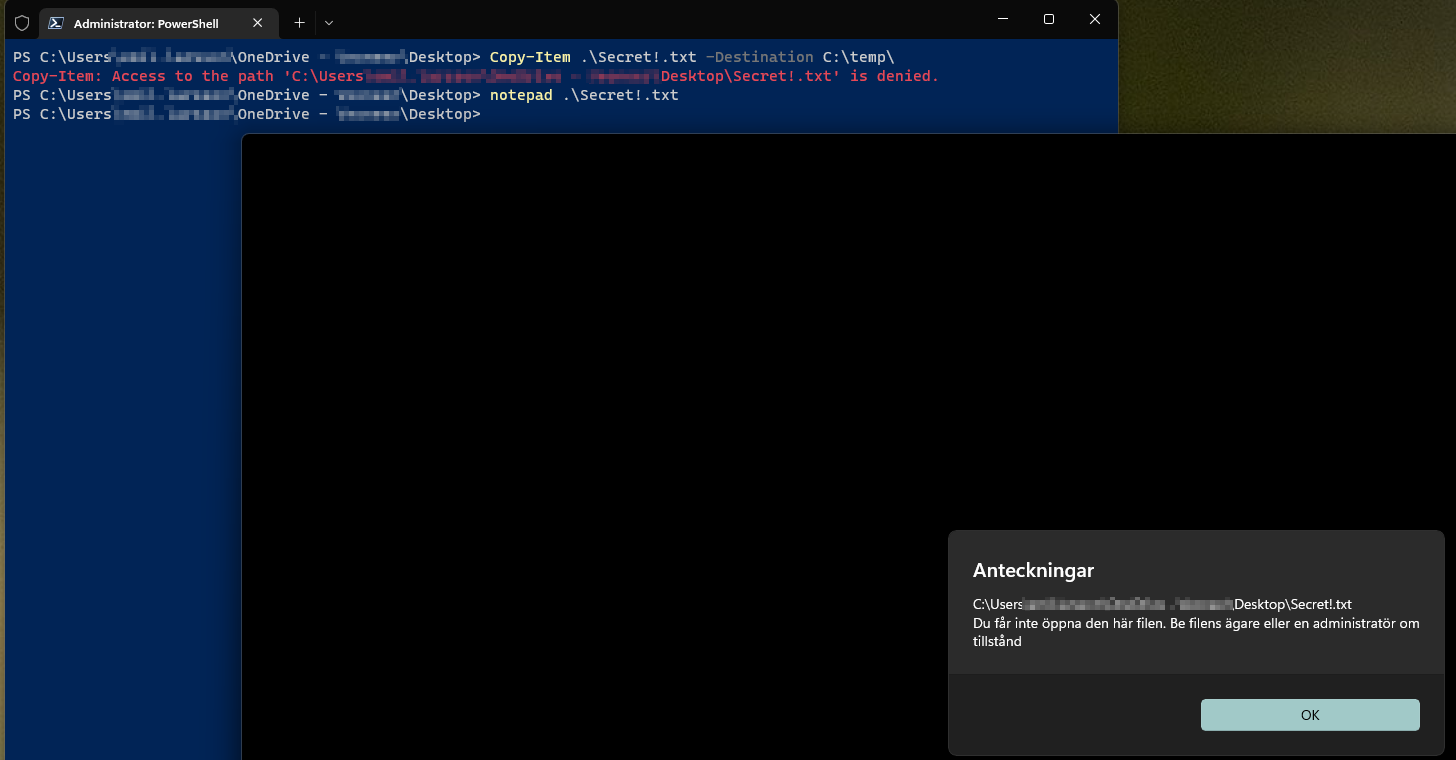
The screenshot displays an attempt to move the file, as well as open it with notepad. Both failed due to a “lack of access”.
- Restoring the certificate using the public key in LocalMachine store
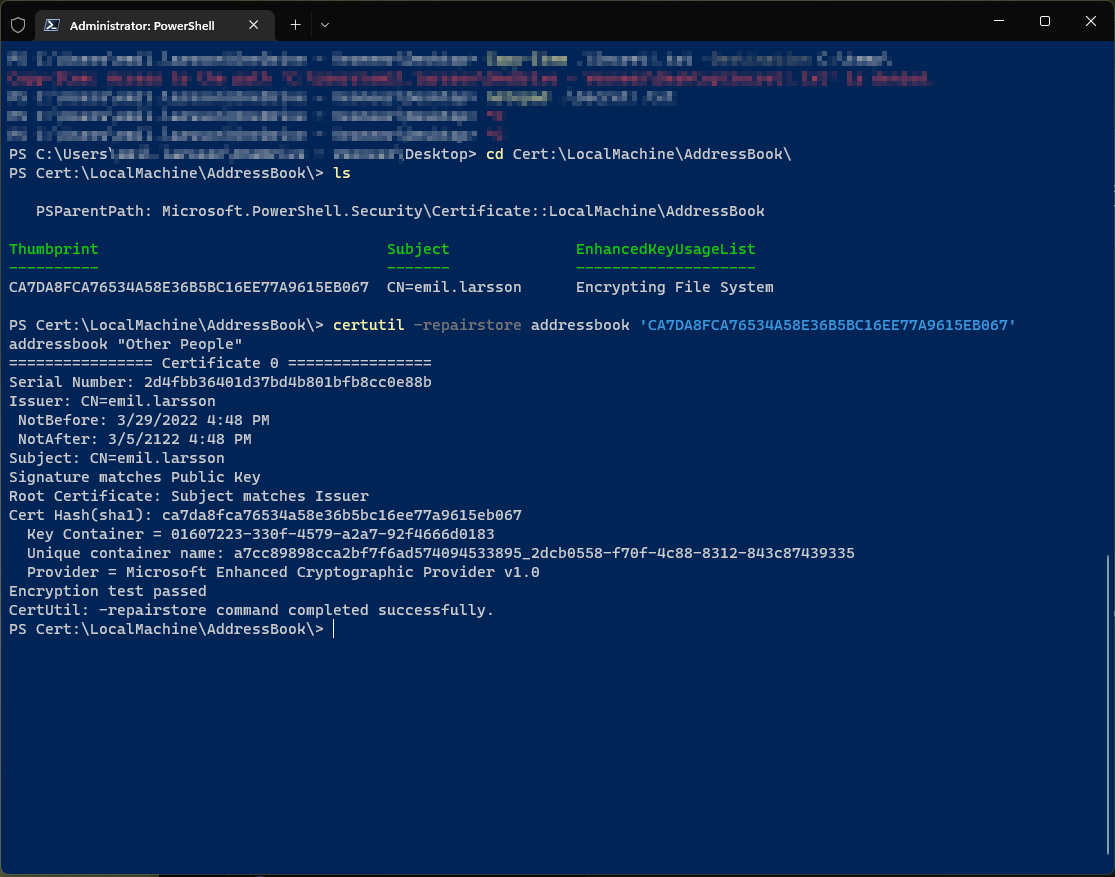
First, we move into the LocalMachine\AddressBook path in the certificate store, and we verify that it contains our public-key based certificate
We then utilize certutil to restore the private-key part of that we had before lost:
certutil -repairstore addressbook '<insert thumbprint>'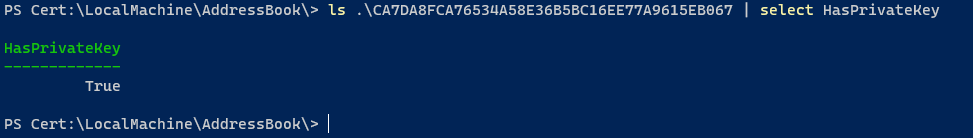
Verify that the PrivateKey was infact restored
We have now restored the most critical part of the removal, but decryption will still fail, since windows will only query your personal store while the decryption process takes place. This means we will need to export this certificate, together with it’s private key - and import it to your personal store.
- Export / Import the key-pair to the Personal Store
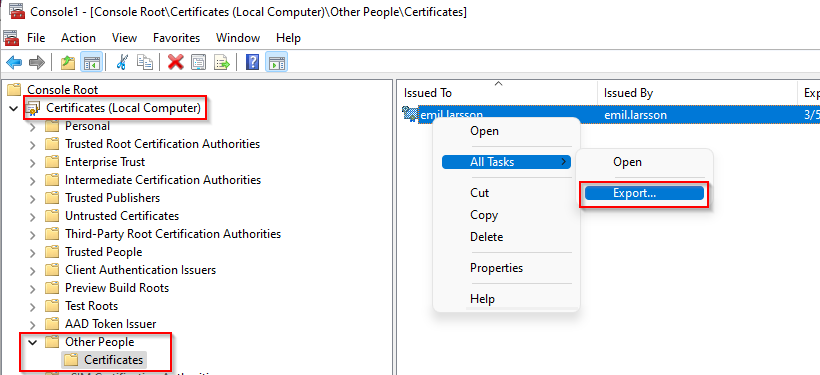
Navigate to the mmc snap-in, import the Certificate snap-in, select Local Computer, and navigate to the ‘Other People’ folder
Right-click the certificate (this is the same certificate that we displayed in PowerShell after the restore process) All Tasks > Export…
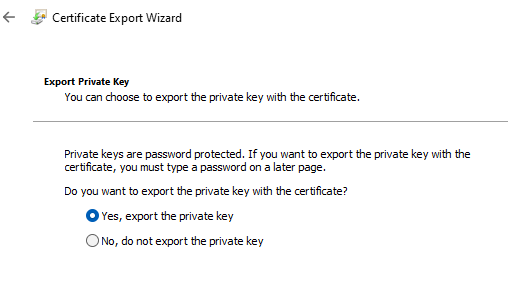
Export the private key > Next
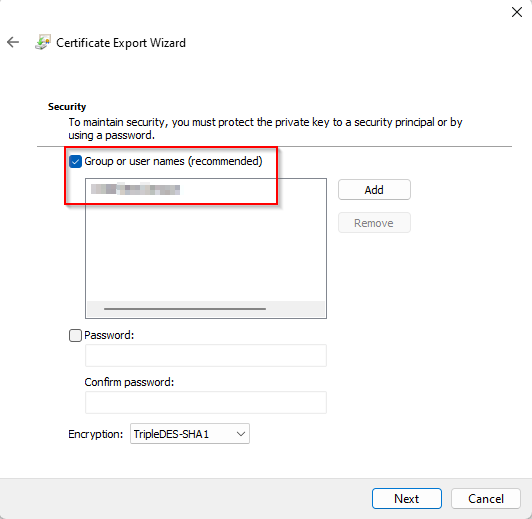
Use your currently logged on user > Next
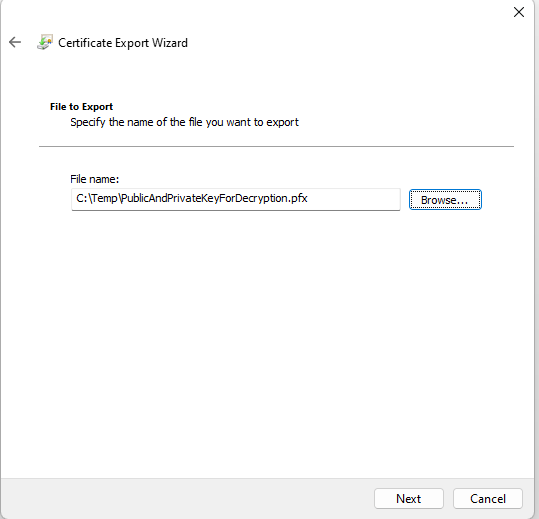
Save to path
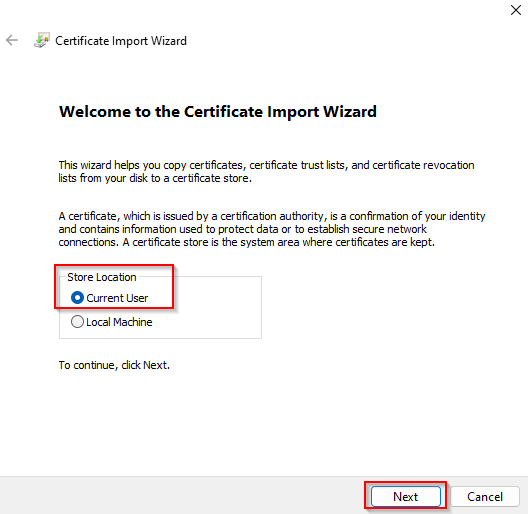
Navigate to the path, right-click > Install PFX, Current User > Next > Next > Next..
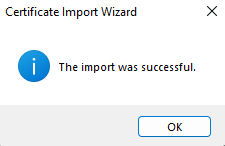
We have now moved the key-pair back to the personal store, and can now decrypt files
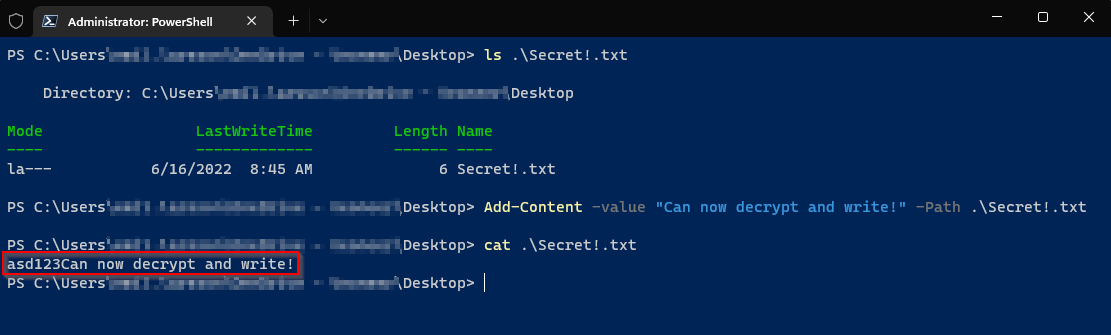
Verifying this by writing to the file, and getting it’s content
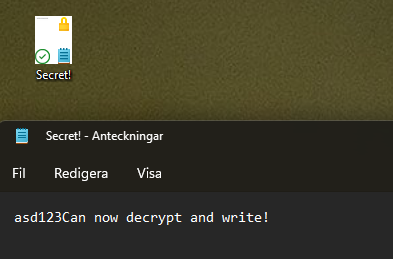
Double-clicking the file now works as expected
Discussion
We have now simulated an issue that unaware users can be exposed to, and solved it using PowerShell, the Certificate snap-in in mmc, and certutil.
Accidential deletion the private/public key-pair in the personal store can be quite common, since IT personel usually perform this, together with a GPUpdate, to re-enroll autoenrollment managed certificates. However, in this case the certificate will not re-enroll itself since it’s a self-signed certificate, only used locally for ecryption/decryption.
This problem be solved in this way for self-signed certificates, I would imagine that it’s the most of cases.
If your Public Key Infrastructure enrolls “Encryption File System” certificates to domain users, a PKI admin could in theory export the certificate in the CA (as long as the private key is exportable, that is).